In a Rhino Safety Labs, six crucial vulnerabilities have been recognized in Infoblox’s NetMRI community automation and configuration administration answer, particularly model 7.5.4.104695 of the digital equipment.
These safety flaws, starting from unauthenticated command injection to hardcoded credentials and arbitrary file learn as root, pose extreme dangers to organizations counting on NetMRI for community administration.
If exploited, these vulnerabilities may allow attackers to achieve full administrative entry, probably compromising total community infrastructures.
Extreme Flaws Expose Community Automation Instrument
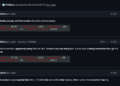
The analysis highlights an unauthenticated command injection vulnerability (CVE-2025-32813) within the get_saml_request endpoint, the place inadequate sanitization of the saml_id parameter permits attackers to execute arbitrary working system instructions.
By crafting a malicious URL, an attacker can run instructions like whoami and even escalate to root privileges utilizing sudo /bin/sh, due to a permissive entry within the /and many others/sudoers file.
One other alarming flaw, an unauthenticated SQL injection (CVE-2025-32814), exists within the login web page’s skipjackUsername parameter, enabling attackers to extract delicate information reminiscent of cleartext admin passwords by error-based SQL payloads.
Moreover, hardcoded credentials (CVE-2025-32815) present in configuration information grant entry to inside endpoints, which may be exploited for cookie forgery, in the end resulting in admin privilege escalation.
That is achieved by injecting malicious session information into cookie information by way of weak endpoints like SetRawCookie.tdf, tricking the system into recognizing the attacker as an admin consumer.
Complete Exploits Detailed for Potential Threats
Additional deepening the menace, the disclosure reveals a hardcoded Ruby cookie secret key that facilitates distant code execution (RCE) by crafting malicious session cookies, a recognized Rails vulnerability exploited by way of Metasploit modules to achieve a root shell.
Authenticated customers, or attackers with cast cookies, can exploit an arbitrary file learn vulnerability (CVE-2024-54188) by the ViewerFileServlet, accessing delicate system information like /and many others/shadow as root.
Lastly, an authenticated SQL injection (CVE-2024-52874) within the Run.tdf endpoint permits additional information extraction, compounding the chance for compromised techniques.
These interconnected flaws create a harmful assault chain, the place an preliminary unauthenticated exploit can cascade into full system takeover with out requiring prior entry privileges.
Infoblox has responded to those findings, with fixes carried out in NetMRI model 7.6.1, as confirmed of their data base articles launched alongside the general public disclosure on June 4, 2025.
The vulnerabilities had been first reported to Infoblox PSIRT on September 18, 2024, with an in depth timeline of acknowledgment, validation, and CVE assignments culminating in patches for affected techniques.
In line with the Report, Rhino Safety Labs has additionally printed proof-of-concept code on their GitHub repository, emphasizing the urgency for organizations to replace their techniques.
For community directors, this serves as a stark reminder of the crucial have to patch and monitor community administration instruments, that are prime targets because of their intensive entry throughout infrastructures.
Failure to handle these vulnerabilities may lead to catastrophic breaches, exposing delicate configurations and probably resulting in widespread community compromise.
Instant motion to improve to the mounted model and evaluate entry logs for suspicious exercise is strongly suggested to mitigate these high-severity dangers.
To Improve Your Cybersecurity Abilities, Take Diamond Membership With 150+ Sensible Cybersecurity Programs On-line – Enroll Right here